Threat actors have targeted industrial suppliers in Japan and several European countries in sophisticated attacks that employed various techniques to make malware detection and analysis more difficult, Kaspersky’s ICS CERT unit reported on Thursday.
The first attacks were spotted in early 2020 and, as of early May, Kaspersky has seen targeted organizations in Japan, Italy, Germany and the UK. The cybersecurity firm says the targets supply equipment and software for industrial organizations, particularly for the energy sector.
Kaspersky said its products blocked the malware in each of the attacks it observed, and the company currently does not know what the hackers’ goals are.
“We may only guess that focus on the power and energy organization suppliers may suggest the attackers are seeking an entry point into power and energy enterprises,” Evgeny Goncharov, Head of Kaspersky ICS CERT, told SecurityWeek.
Goncharov said they detected malicious activity on IT systems, but not in OT networks. The attackers have apparently been trying to steal authentication credentials.
Learn more about threats to industrial systems at SecurityWeek’s 2020 ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
According to Kaspersky, the attacks start with a phishing email sent to the targeted organization. These emails are customized and written in the target’s language, and the malware only starts conducting its activities after ensuring that the operating system language on the compromised machine matches the language in the phishing email.
The phishing emails carry a Microsoft Office document containing a malicious macro script which, when triggered by the victim, decrypts and executes a PowerShell script. This script is designed to download an image from image hosting services such as Imgur or imgbox — the URL of the image is randomly selected from a list.
The image contains data that is extracted by the malware to generate another PowerShell script, which in turn creates yet another PowerShell script that is an obfuscated version of Mimikatz, the popular password-stealing tool.
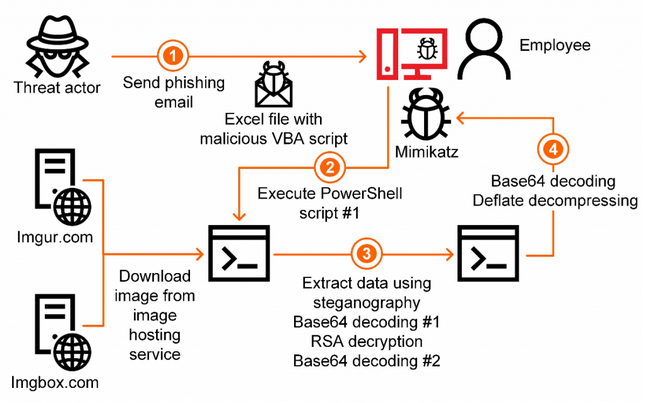
Kaspersky has pointed out that the use of steganography to hide malicious code in an image and the use of legitimate services to host that image “makes it virtually impossible to detect such malware using network traffic monitoring and control tools while it is being downloaded.”
Another interesting technique observed in these attacks involves the use of an exception message as the decryption key for a malicious payload.
“This technique can help the malware evade detection in automatic analysis systems of the sandbox class and makes analyzing the functionality of the malware significantly more difficult for researchers if they do not know what language pack was used on the victim’s computer,” Kaspersky said.
“The use of the above techniques, combined with the pinpoint nature of the infections, indicates that these were targeted attacks. It is a matter of concern that attack victims include contractors of industrial enterprises. If the attackers are able to harvest the credentials of a contractor organization’s employees, this can lead to a range of negative consequences, from the theft of sensitive data to attacks on industrial enterprises via remote administration tools used by the contractor,” the company added.
Related: Design Weaknesses Expose Industrial Systems to Damaging Attacks















