
What are MFA fatigue attacks and how can they be prevented?
Recent high-profile cyberattacks have demonstrated the effectiveness of an interesting method for getting past multi-factor authentication (MFA).
MFA provides an extra layer of security for user accounts. If a threat actor can obtain an account’s username and password through phishing or other methods, MFA should prevent them from accessing the account.
There are several types of MFA and attackers can use various methods to bypass this security layer. They can exploit MFA bypass vulnerabilities, use social engineering to trick the target into providing the one-time password, deploy phishing pages that harvest not only the username and password but also the MFA code, they can use malware that collects MFA codes, or hijack the victim’s phone number via SIM swapping to receive the codes meant for the target.
In recent months, there appears to have been an increase in attacks that rely on a method known as ‘MFA fatigue’ and ‘MFA push notification spam’.
This method targets MFA that relies on push notifications, where the user gets a push notification on their mobile device asking them to approve a login attempt after their username and password have been entered.
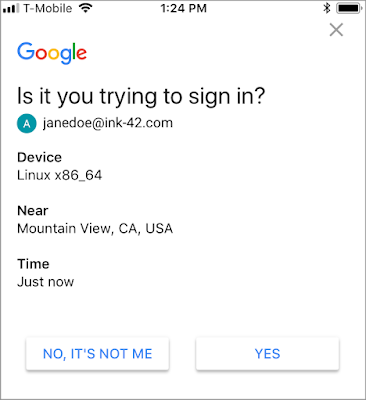
SMS-based multi-factor authentication has been proven to be insecure and many online services providers have replaced it with more secure alternatives. One of them is push notifications, which are displayed to the user either by the app associated with the service they want to access, or by a dedicated third-party app that works with multiple services.
While users would likely not approve the login if they only got one suspicious push notification, many users would and do approve them if they’re inundated with notifications.
Continuously getting MFA push notifications might lead the user to believe that there is a glitch and approving the request could put an end to the spamming. The victim could also approve the request accidentally. As soon as they hit the ‘Yes, it’s me’ button, the attacker can log into their account and perform malicious actions.
[ Read: Why Are Users Ignoring Multi-Factor Authentication? ]
This method was leveraged in the recent attacks targeting Cisco and Uber. In the attack on Uber, the attacker increased their chances of success by combining it with social engineering. They contacted the victim on WhatsApp, claiming to be a member of the IT team and instructing them to approve the login to get the MFA notifications to stop.
Uber linked the attack to individuals associated with the Lapsus$ group, which over the past year targeted companies such as NVIDIA, Okta, Globant, Samsung, Vodafone, Ubisoft and Microsoft. A suspect was arrested in the United Kingdom shortly after the incident came to light.
Microsoft also reported seeing the Lapsus$ group use MFA fatigue, but it’s unclear if the method was also used in the attack aimed at the tech giant.
A ransomware gang took credit for the recent Cisco hack, but the networking giant attributed the attack to an access broker that is also known to have ties to the Lapsus$ group.
The same method has also been used by state-sponsored threat actors. Mandiant reported last year that the Russian threat group known as APT29 and Nobelium had used MFA fatigue in attacks aimed at governments and businesses.
Preventing MFA fatigue attacks
Several cybersecurity companies have shared recommendations on mitigating the threat posed by MFA fatigue, including Malwarebytes, CyberArk and Arctic Wolf.
Employee training is important for addressing the risk of MFA fatigue attacks. They need to be aware of such attacks, and they should be instructed to immediately notify the organization’s IT or security team if they receive many push notifications. They should also be aware that messages or phone calls allegedly coming from their IT department could actually originate from the attacker.
Organizations can prevent such attacks by using rate limiting mechanisms that block authentication to an account that is hit by a large number of push requests.
The risk can also be reduced by using number matching in MFA authentication. This involves the user being required to enter a number displayed on the desktop/laptop screen before pressing the ‘Yes, it’s me’ button on their mobile device. In the case of an attack, the victim does not see the number so they cannot approve the request.
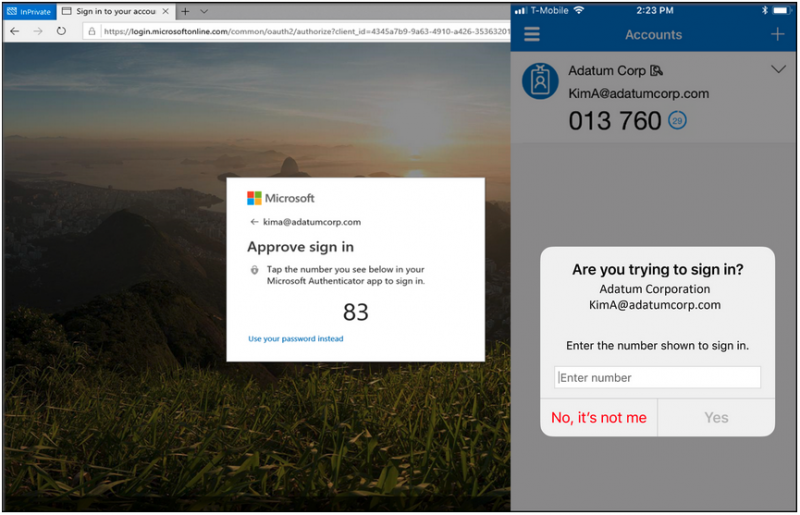
If an account breach could have serious consequences, organizations should disable the use of MFA push notifications and only allow employees to use more secure authentication methods, such as challenge-response or time-based one-time password verification.
Another recommendation involves the use of FIDO2 (WebAuthn) hardware security keys, which are not vulnerable to phishing and push notification spam.
Some identity solutions providers, such as Duo and Okta, say their solutions can detect and prevent MFA fatigue attacks.
Related: US Warns About Russian Attacks Exploiting MFA Protocols, PrintNightmare Flaw
Related: Group Behind SolarWinds Hack Bypassed MFA to Access Emails at US Think Tank
Related: Reality Check on the Demise of Multi-Factor Authentication













