
A significant percentage of the malware seen last year on USB drives used in industrial facilities was capable of targeting and disrupting industrial control systems (ICS), according to a report published this week by Honeywell.
The industrial giant has published its fourth annual report focusing on the malware found by one of its dedicated security products on the USB drives that were brought into its customers’ industrial environments.
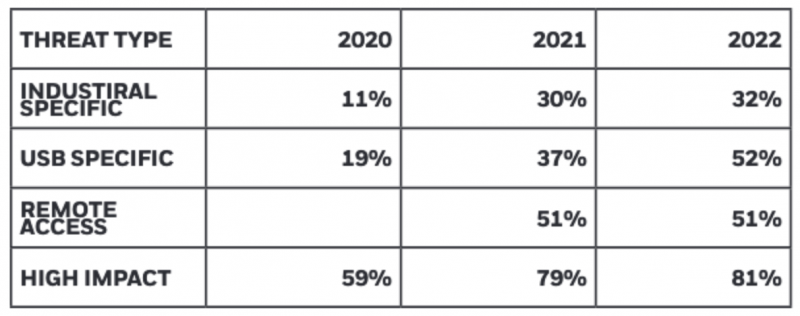
Honeywell’s analysis of the data found that the percentage of industrial-specific malware has increased to 32%, from 30% in the 2021 report and 11% in the 2020 report. The percentage of malware designed to propagate over USB or to specifically exploit USB for infection increased to 52%, significantly higher than the 37% seen in 2021.
There has also been a slight increase in malware that can cause disruption to operational technology (OT) systems — this includes loss of control or loss of view. Specifically, 81% of the malware detected by Honeywell’s product on USB drives was disruptive, up from 79% in 2021.
Learn More About ICS Threats at SecurityWeek’s 2022 ICS Cyber Security Conference
The company found that more than three-quarters of the malware were trojans, and 51% — the same as in the previous year — provided remote access or remote control capabilities.
“This solidifies our suspicion that adversaries are deliberately leveraging USB removable media as an initial attack vector, at which point they will attempt to establish remote connectivity to download additional payloads, exfiltrate data, and establish command and control,” the company said.
“USB-borne malware is clearly being leveraged as part of larger cyber attack campaigns against industrial targets. Adaptations have occurred to take advantage of leveraging the ability of USB removable media to circumvent network defenses and bypass the air gaps upon which many of these facilities depend on for protection. Continued diligence is necessary to defend against the growing USB threat, and strong USB security controls are highly recommended,” Honeywell concluded.
More information, as well as recommendations for organizations, can be found in the 2022 Honeywell Industrial Cybersecurity USB Threat Report (PDF).
Related: Russia-Linked Pipedream/Incontroller ICS Malware Designed to Target Energy Facilities
Related: U.S. Warns Sophisticated ICS/SCADA Malware Can Damage Critical Infrastructure
Related: Ransomware Often Hits Industrial Systems, With Significant Impact















